{{item.title}}
{{item.text}}

{{item.text}}
Claudia Hösli
Cybersecurity and Privacy, PwC Switzerland
The Society for Worldwide Interbank Financial Telecommunication (SWIFT) provides secure global payment services worldwide. In 2017, it launched the Customer Security Programme (SWIFT CSP) as a targeted measure to combat cyber-attacks. Since last year, SWIFT requires a compulsory independent assessment on the implementation of its mandatory controls and has further expanded the SWIFT CSP for 2022.
The SWIFT CSP is a security programme for SWIFT participants with the aim of ensuring an appropriate level of security for the participants’ local SWIFT infrastructure. With this framework for coordinated quality assurance, SWIFT aims to address increasing cyber risks and strengthen the defensive capabilities of SWIFT participants against cyber-attacks. For 2022, SWIFT has introduced one new mandatory control and one mandatory component “Customer Connector” for participants with an A4 SWIFT architecture to the framework.
At PwC, we help clients evaluate their ability to deal with the main cyber risks and threats of the digital world in an easy and understandable way.
In 2021, SWIFT participants had to complete an independent assessment in accordance with SWIFT requirements for the first time. Experience from these assessments has shown that ongoing compliance with the SWIFT CSP requirements requires a great deal of efforts on the part of SWIFT participants. This is because the SWIFT requirements are very extensive and also affect the local IT infrastructure of the participants. Furthermore, for some institutions, the individual SWIFT requirements go beyond their internal security requirements.
As SWIFT announced in a February 2022 release, more than 89 percent of all SWIFT participants responsible for more than 99 percent of SWIFT network traffic have attested compliance with the controls. SWIFT also reserves the right to inform local regulators on SWIFT participants that are not yet or incompletely attested. See also here.
While our assessments last year showed that SWIFT participants addressed most SWIFT CSP controls and that a vast majority of our clients complied with SWIFT CSP controls, we also identified some exceptions. Most of these are observed in the field of control 7.1 “Cyber Incident Response Planning” due to missing testing of the cyber incident response plan and for control 6.4 “Logging and Monitoring” due to a lack of concrete measures to monitor SWIFT user activities.
New SWIFT Customer Security Program (CSP) requirements: Are you ready for your 2022 attestation? Together with Laetitia Cailliez, Head of Exchange Operations and International Payments, Credit Agricole Payment Services, and Olivier Dazard, SWIFT, we shed light on the SWIFT CSP and provided a retrospective on 2021.
Legend:
1: Restrict internet access and protect critical systems from general IT environment
2: Reduce attack surface and vulnerabilities
3: Physically secure the environment
4: Prevent compromise of credentials
5: Manage identities and separate privileges
6: Detect anomalous activity to systems or transaction records
7: Plan for incident response and information sharing
SWIFT adapts its security programme every year to the current circumstances. For 2022, there are two main changes in the mandatory controls (figure 2):
Figure 2: Overview of key CSP updates for 2022
For the 2022 attestation cycle, the new SWIFT requirements need to be addressed proactively. Participants should deal with the upgraded and new mandatory controls extensively and at an early stage. For this purpose, we recommend to check the SWIFT website for a detailed overview of the CSP programme, as the new features may not yet be included in the local security architecture. This means that SWIFT participants may have to implement new control measures and test their effectiveness. Do it soon – it is important to take enough time and start the assessment and preparation for it early on.
It is also advisable to look ahead to the advisory controls, as some of them may tend to be upgraded to mandatory controls next year. For 2023, this mainly concerns control 1.5A “Customer Environment Protection” as well as controls 6.2 “Software Integrity” and 6.3 “Database Integrity” for architecture type A4.
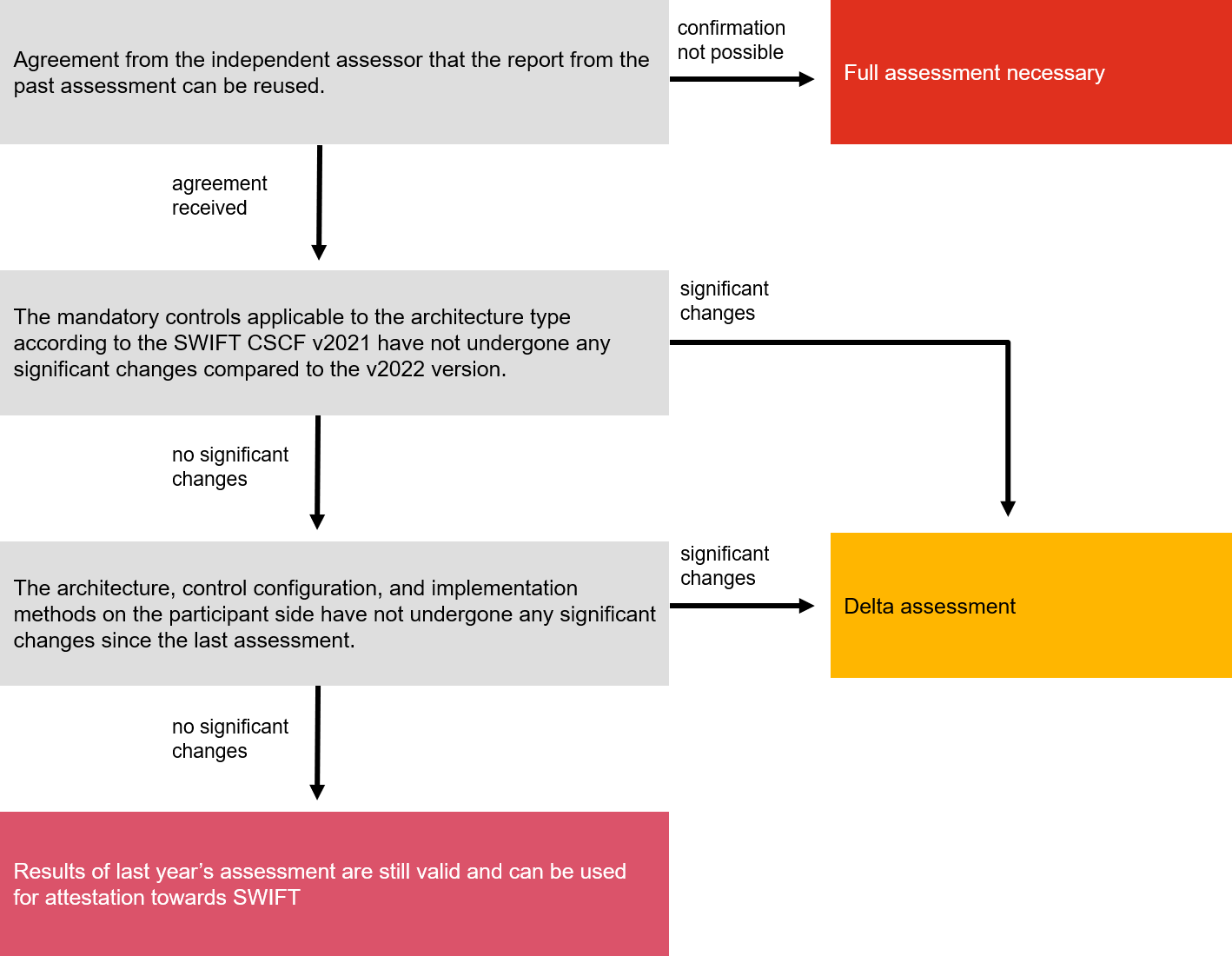
Although the performance of an independent assessment has been mandatory for all SWIFT participants since 2021, under certain conditions SWIFT allows the independent assessment report to be used for two years or a delta assessment to be conducted. It is therefore not necessary to make the full effort for the independent assessment every year. The following overview shows the different possibilities.
Figure 3: Assessment tree
The proper implementation of SWIFT requirements is easier to demonstrate with a structured approach. At PwC we work in various roles for various SWIFT participants (figure 4). In this way, we help SWIFT participants to design their information and cybersecurity in accordance with the rules, especially under time pressure, and to refine their SWIFT compliance in a targeted manner.
Figure 4: External help for proving SWIFT compliance
SWIFT continues to fight cyber threats. With the security programme SWIFT CSP, it issues binding and optional requirements to protect the local SWIFT infrastructure. For 2022, SWIFT has upgraded one previously optional control (“advisory”) to a mandatory control (“mandatory”) and added the “Customer Connector” for architecture type A4 as a mandatory component for the affected controls.
Due to the high relevance of the subject of cybersecurity and to meet the SWIFT requirements this year – and to carry out the attestation on time –, it is worth prioritising the subject.
Involving a competent third party in the assessment provides more security, allows comparison, and identifies potential for improvement. This year, however, less effort can be expected as SWIFT allows the re-use of an assessment report for two years.
#social#
If you are interested in a personal exchange, please do not hesitate to contact us.
https://pages.pwc.ch/core-contact-page?form_id=7014L000000NM93QAG&embed=true&lang=en
At PwC, we are a community of solvers – powered by technology – committed to helping you protect everyone, and everything, you care about.
{{item.text}}

{{item.text}}