{{item.title}}
{{item.text}}

{{item.text}}
Claudia Hösli
Cybersecurity and Privacy, PwC Switzerland
Benoit de Jocas
Cybersecurity and Privacy, PwC Switzerland
The Society for Worldwide Interbank Financial Telecommunication (SWIFT) provides secure global payment services worldwide. SWIFT is successively strengthening its Customer Security Programme (SWIFT CSP) as a targeted measure to combat cyber attacks. In the meantime, the Swiss National Bank (SNB) has introduced a cybersecurity controls framework to establish a baseline of cybersecurity controls for the participants in the Swiss Interbank Clearing payment system (SIC system) infrastructure.
The SWIFT CSP is a security programme for SWIFT participants designed to maintain an appropriate level of security for participants’ local SWIFT infrastructure. With this coordinated quality assurance framework, SWIFT aims to address the growing cyber risks and strengthen the defensive capabilities of SWIFT participants against cyber attacks.
At PwC, we help clients evaluate their ability to deal with the main cyber risks and threats of the digital world in an easy and understandable way.
The Swiss National Bank (SNB) issued its own cybersecurity controls framework for participants in the SIC system in late 2022. The SNB has adopted a similar approach to SWIFT and defined a set of 17 controls, with 15 of them categorised as “mandatory”. Institutes that connect to the SIC system through their SWIFT infrastructure will likely already have their SIC requirements covered by the SWIFT CSP attestation. However, clients who connect to the SIC system via a dedicated infrastructure may need to put more implementation efforts to comply with the SIC system controls framework.
By the end of 2023, the SNB will ask participants to provide a status update on their implementation of the SIC requirements. By the end of 2024, the first official independent attestation will be mandatory for all SIC participants. The attestation must be provided by an independent function (e.g. internal audit or external audit firm).
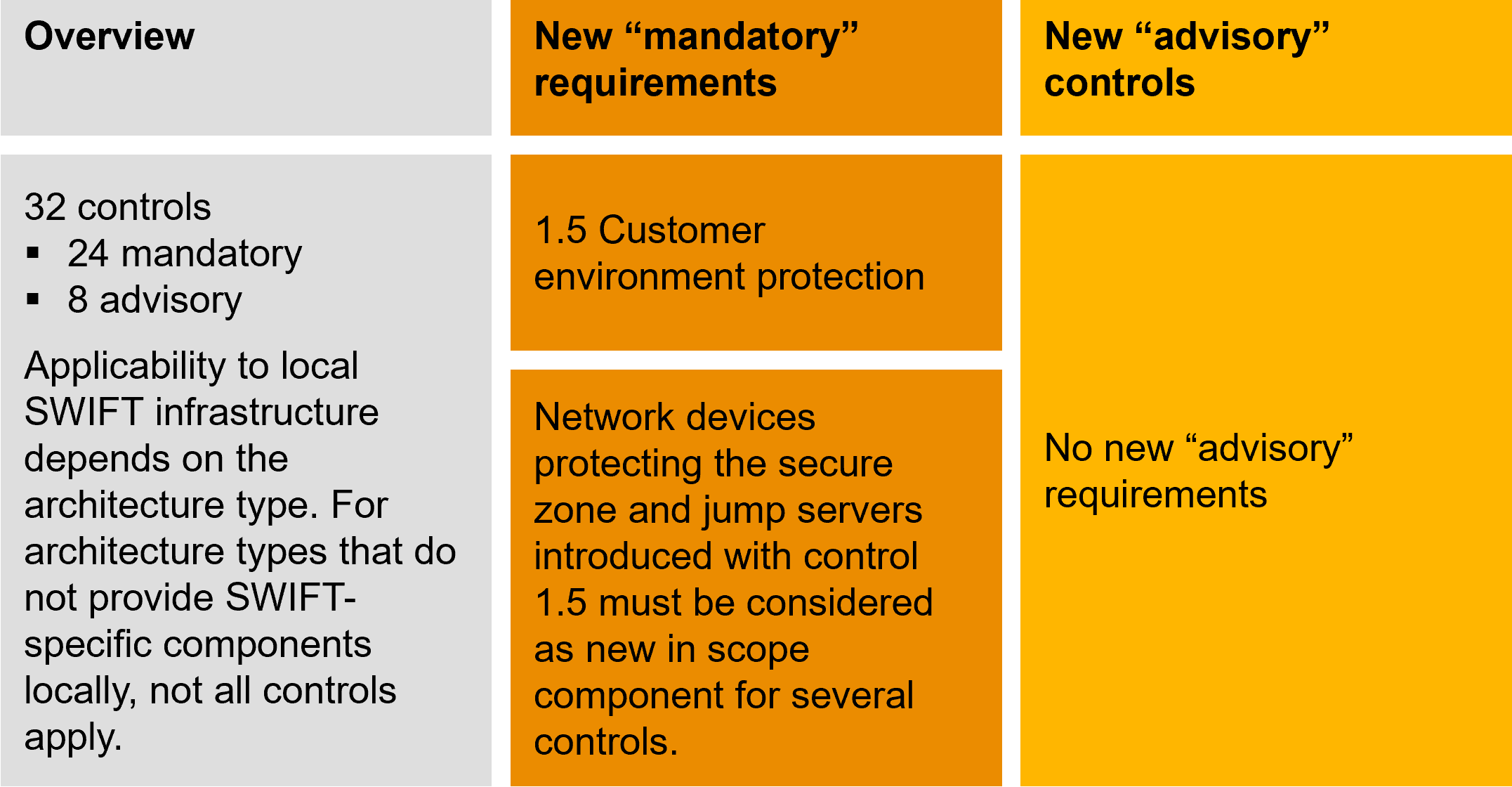
SWIFT adjusts its security programme annually to align with current circumstances. In 2023, participants with an A4 architecture type are the ones most affected by the changes. Specifically, control 1.5 “Customer Environment Protection” has been designated as a “mandatory” control for the A4 architecture type participants in 2023. This control requires participants to ensure the protection of their connectivity infrastructure from external threats and potential compromises within the general IT environment. Participants are required to establish a dedicated and segregated secure zone for their local connectivity infrastructure or reuse an existing secure zone while implementing the SWIFT CSP requirements. This includes implementing robust access controls for secure zone entry and traffic restrictions, among other measures.
Figure 1: Overview of key CSP updates for 2023
Participants are advised to familiarise themselves with the new requirements in a timely manner in order to allow sufficient time for implementation. Considering that new features may not have been incorporated into the local security architecture yet and that time is needed to implement new technical measures and test their effectiveness, we recommend SWIFT participants to begin early. For this purpose, please refer to the detailed description of the SWIFT CSP content available on the SWIFT website.
As for SIC participants, it is important for them to acquaint themselves with the SIC cybersecurity controls framework and assess whether there are any gaps in meeting the control requirements.
Independent assessments have been mandatory for all SWIFT participants since 2021. However, SWIFT does allow the use of the independent assessment report for two years or a delta assessment under certain conditions. This means that a full independent assessment is not necessary every year.
The following overview outlines the different possibilities.
Figure 2: Assessment tree
Most participants probably conducted a full assessment in 2021 and a delta assessment in 2022, resulting in another full assessment in 2023. An adequate implementation of the SWIFT and SIC system requirements can be more easily demonstrated through a structured approach.
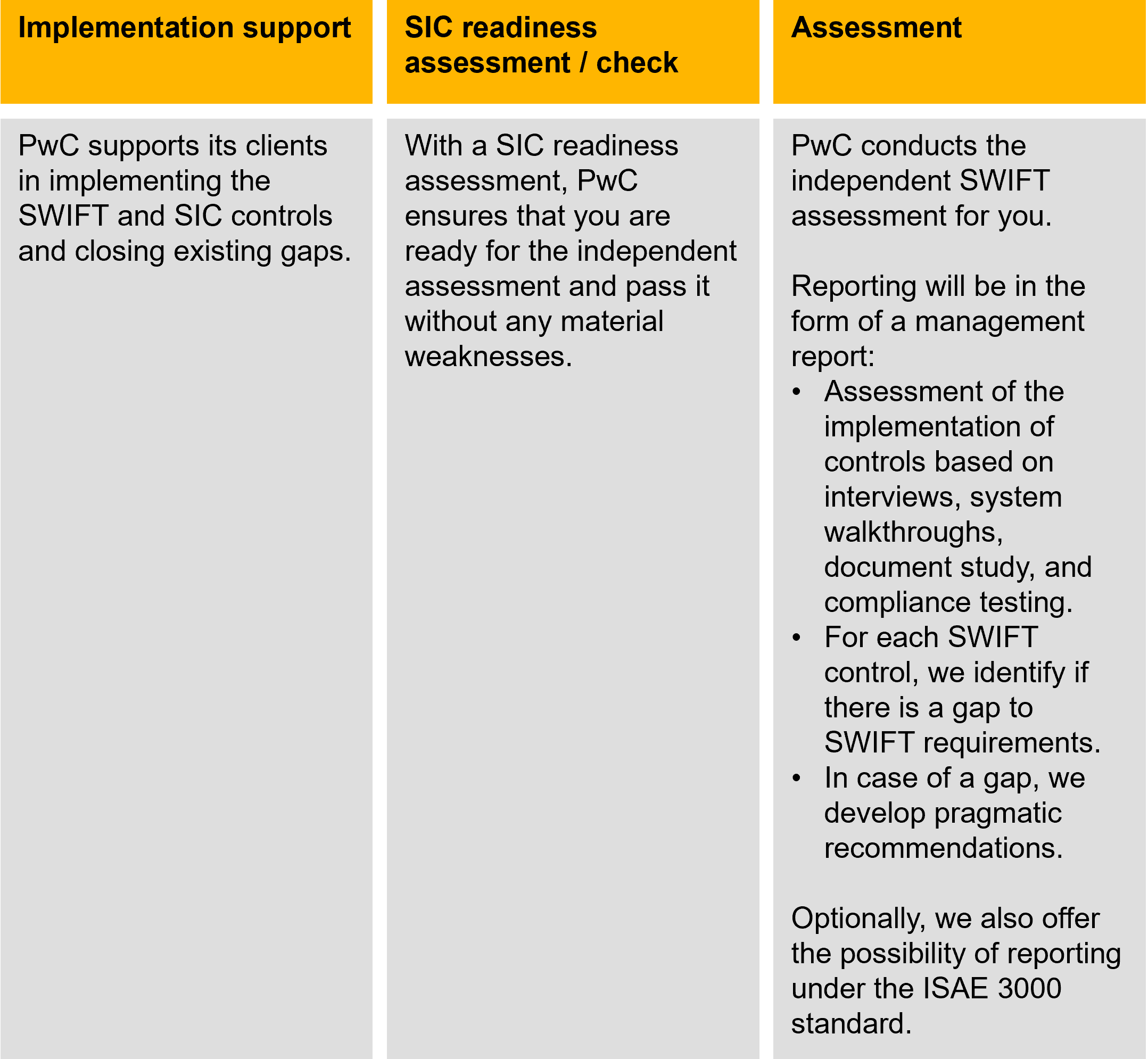
At PwC, we work in various roles for many SWIFT and SIC system participants (see Figure 3). With our extensive knowledge of market practices, we can help ensure that participants’ cybersecurity practices are compliant, particularly under time pressure, and assist in refining their SWIFT and SIC system compliance in a targeted manner.
Figure 3: External help for independent proof of SWIFT and SIC compliance
SWIFT continues to fight cyber threats. Through the SWIFT CSP security programme, it issues mandatory and optional requirements to safeguard the local SWIFT infrastructure. In 2023, one previously optional control (“advisory”) has been upgraded to a mandatory control (“mandatory”).
Following SWIFT's lead, the SNB published its own cybersecurity controls framework for endpoint security in the SIC system in late 2022. SIC system participants are expected to submit a status report on requirement implementation by the end of 2023 and undergo their first independent attestation by the end of 2024. Overall, the SIC system control requirements are very similar to those of the SWIFT CSP.
Given the high relevance of cybersecurity and the need to meet both SWIFT and SIC requirements while ensuring timely completion of the attestation, it is worth to prioritise this topic.
Involving a competent third party in the assessment provides greater assurance, establishes a benchmark, and identifies potential areas for improvement.
#social#
If you are interested in a personal exchange, please do not hesitate to contact us.
https://pages.pwc.ch/core-contact-page?form_id=7014L000000DZFaQAO&embed=true&lang=en
Trust in a team that truly helps your organisation transform by designing, implementing, and continuously monitoring the right cybersecurity solutions. Together, we create sustainable value and trust – now and in the future.
{{item.text}}

{{item.text}}